TM01: Infrastructure-Based Traffic Surveillance
This service package includes traffic detectors, other surveillance equipment, the supporting field equipment, and Center to Field communications to transmit the collected data back to the Traffic Management Center. The derived data can be used locally such as when traffic detectors are connected directly to a signal control system or remotely (e.g., when a CCTV system sends data back to the Traffic Management Center). The data generated by this service package enables traffic managers to monitor traffic and road conditions, identify and verify incidents, detect faults in indicator operations, and collect census data for traffic strategy development and long range planning. The collected data can also be analyzed and made available to users and the Traveler Information Center physical object.
Relevant Regions: Australia, Canada, European Union, and United States
- Enterprise
- Functional
- Physical
- Goals and Objectives
- Needs and Requirements
- Sources
- Security
- Standards
- System Requirements
- Implementations
Enterprise
Development Stage Roles and Relationships
Installation Stage Roles and Relationships
Operations and Maintenance Stage Roles and Relationships
(hide)
| Source | Destination | Role/Relationship |
|---|---|---|
| Basic Vehicle Maintainer | Basic Vehicle | Maintains |
| Basic Vehicle Manager | Basic Vehicle | Manages |
| Basic Vehicle Owner | Basic Vehicle Maintainer | System Maintenance Agreement |
| Basic Vehicle Owner | Basic Vehicle Manager | Operations Agreement |
| Basic Vehicle Owner | ITS Roadway Equipment Maintainer | Maintenance Data Exchange Agreement |
| Basic Vehicle Owner | ITS Roadway Equipment Owner | Expectation of Data Provision |
| Basic Vehicle Owner | ITS Roadway Equipment User | Service Usage Agreement |
| Basic Vehicle Supplier | Basic Vehicle Owner | Warranty |
| ITS Roadway Equipment Maintainer | ITS Roadway Equipment | Maintains |
| ITS Roadway Equipment Manager | ITS Roadway Equipment | Manages |
| ITS Roadway Equipment Owner | ITS Roadway Equipment Maintainer | System Maintenance Agreement |
| ITS Roadway Equipment Owner | ITS Roadway Equipment Manager | Operations Agreement |
| ITS Roadway Equipment Owner | Other ITS Roadway Equipment Maintainer | Maintenance Data Exchange Agreement |
| ITS Roadway Equipment Owner | Other ITS Roadway Equipment Owner | Information Exchange and Action Agreement |
| ITS Roadway Equipment Owner | Other ITS Roadway Equipment User | Service Usage Agreement |
| ITS Roadway Equipment Owner | Traffic Management Center Maintainer | Maintenance Data Exchange Agreement |
| ITS Roadway Equipment Owner | Traffic Management Center Owner | Information Exchange and Action Agreement |
| ITS Roadway Equipment Owner | Traffic Management Center User | Service Usage Agreement |
| ITS Roadway Equipment Owner | Traffic Operations Personnel | Application Usage Agreement |
| ITS Roadway Equipment Supplier | ITS Roadway Equipment Owner | Warranty |
| Other ITS Roadway Equipment Maintainer | Other ITS Roadway Equipment | Maintains |
| Other ITS Roadway Equipment Manager | Other ITS Roadway Equipment | Manages |
| Other ITS Roadway Equipment Owner | ITS Roadway Equipment Maintainer | Maintenance Data Exchange Agreement |
| Other ITS Roadway Equipment Owner | ITS Roadway Equipment Owner | Information Exchange and Action Agreement |
| Other ITS Roadway Equipment Owner | ITS Roadway Equipment User | Service Usage Agreement |
| Other ITS Roadway Equipment Owner | Other ITS Roadway Equipment Maintainer | System Maintenance Agreement |
| Other ITS Roadway Equipment Owner | Other ITS Roadway Equipment Manager | Operations Agreement |
| Other ITS Roadway Equipment Supplier | Other ITS Roadway Equipment Owner | Warranty |
| Traffic Management Center Maintainer | Traffic Management Center | Maintains |
| Traffic Management Center Manager | Traffic Management Center | Manages |
| Traffic Management Center Manager | Traffic Operations Personnel | System Usage Agreement |
| Traffic Management Center Owner | ITS Roadway Equipment Maintainer | Maintenance Data Exchange Agreement |
| Traffic Management Center Owner | ITS Roadway Equipment Owner | Information Provision Agreement |
| Traffic Management Center Owner | ITS Roadway Equipment User | Service Usage Agreement |
| Traffic Management Center Owner | Traffic Management Center Maintainer | System Maintenance Agreement |
| Traffic Management Center Owner | Traffic Management Center Manager | Operations Agreement |
| Traffic Management Center Owner | Transportation Information Center Maintainer | Maintenance Data Exchange Agreement |
| Traffic Management Center Owner | Transportation Information Center Owner | Information Provision Agreement |
| Traffic Management Center Owner | Transportation Information Center User | Service Usage Agreement |
| Traffic Management Center Supplier | Traffic Management Center Owner | Warranty |
| Traffic Operations Personnel | Traffic Management Center | Operates |
| Transportation Information Center Maintainer | Transportation Information Center | Maintains |
| Transportation Information Center Manager | Transportation Information Center | Manages |
| Transportation Information Center Owner | Transportation Information Center Maintainer | System Maintenance Agreement |
| Transportation Information Center Owner | Transportation Information Center Manager | Operations Agreement |
| Transportation Information Center Supplier | Transportation Information Center Owner | Warranty |
| Vehicle Characteristics Maintainer | Vehicle Characteristics | Maintains |
| Vehicle Characteristics Manager | Vehicle Characteristics | Manages |
| Vehicle Characteristics Owner | Vehicle Characteristics Maintainer | System Maintenance Agreement |
| Vehicle Characteristics Owner | Vehicle Characteristics Manager | Operations Agreement |
| Vehicle Characteristics Supplier | Vehicle Characteristics Owner | Warranty |
Functional
This service package includes the following Functional View PSpecs:
Physical
The physical diagram can be viewed in SVG or PNG format and the current format is SVG.SVG Diagram
PNG Diagram
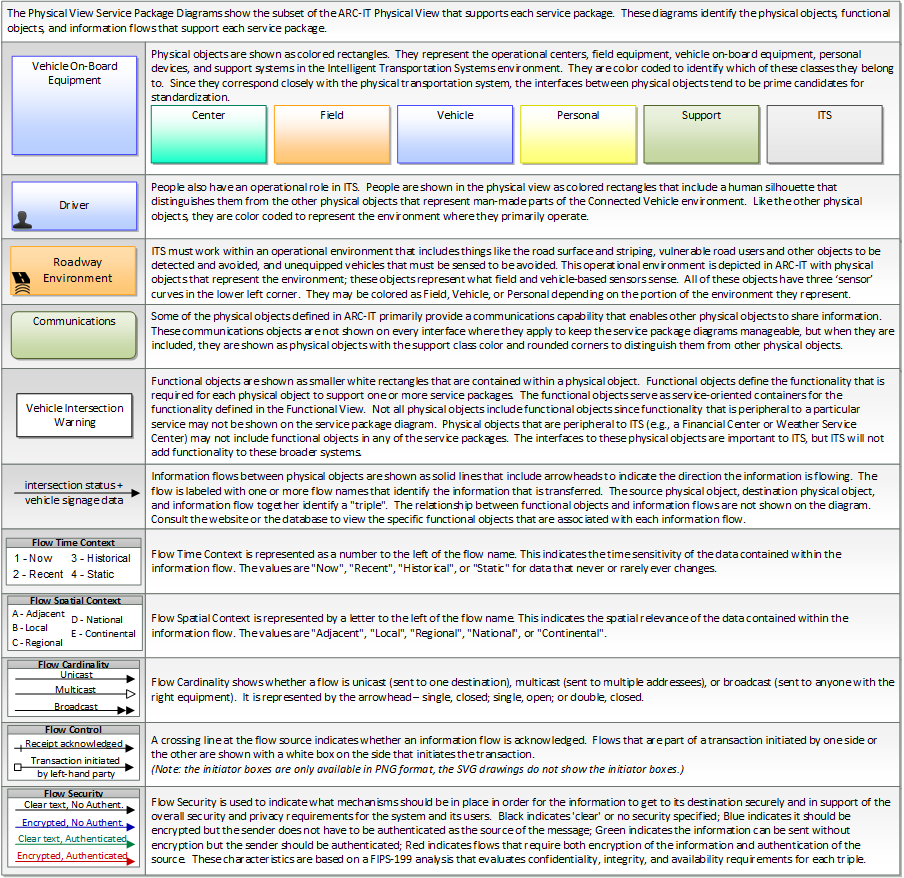
Includes Physical Objects:
| Physical Object | Class | Description |
|---|---|---|
| Basic Vehicle | Vehicle | 'Basic Vehicle' represents a complete operating vehicle. It includes the vehicle platform that interfaces with and hosts ITS electronics and all of the driver convenience and entertainment systems, and other non-ITS electronics on-board the vehicle. Interfaces represent both internal on-board interfaces between ITS equipment and other vehicle systems and other passive and active external interfaces or views of the vehicle that support vehicle/traffic monitoring and management. External interfaces may also represent equipment that is carried into the vehicle (e.g., a smartphone that is brought into the vehicle). Internal interfaces are often implemented through a vehicle databus, which is also included in this object. Note that 'Vehicle' represents the general functions and interfaces that are associated with personal automobiles as well as commercial vehicles, emergency vehicles, transit vehicles, and other specialized vehicles. |
| ITS Roadway Equipment | Field | 'ITS Roadway Equipment' represents the ITS equipment that is distributed on and along the roadway that monitors and controls traffic and monitors and manages the roadway. This physical object includes traffic detectors, environmental sensors, traffic signals, highway advisory radios, dynamic message signs, CCTV cameras and video image processing systems, grade crossing warning systems, and ramp metering systems. Lane management systems and barrier systems that control access to transportation infrastructure such as roadways, bridges and tunnels are also included. This object also provides environmental monitoring including sensors that measure road conditions, surface weather, and vehicle emissions. Work zone systems including work zone surveillance, traffic control, driver warning, and work crew safety systems are also included. |
| Other ITS Roadway Equipment | Field | Representing another set of ITS Roadway Equipment, 'Other ITS Roadway Equipment' supports 'field device' to 'field device' communication and coordination, and provides a source and destination for information that may be exchanged between ITS Roadway Equipment. The interface enables direct coordination between field equipment. Examples include the direct interface between sensors and other roadway devices (e.g., Dynamic Message Signs) and the direct interface between roadway devices (e.g., between a Signal System Master and Signal System Local equipment) or a connection between an arterial signal system master and a ramp meter controller. |
| Traffic Management Center | Center | The 'Traffic Management Center' monitors and controls traffic and the road network. It represents centers that manage a broad range of transportation facilities including freeway systems, rural and suburban highway systems, and urban and suburban traffic control systems. It communicates with ITS Roadway Equipment and Connected Vehicle Roadside Equipment (RSE) to monitor and manage traffic flow and monitor the condition of the roadway, surrounding environmental conditions, and field equipment status. It manages traffic and transportation resources to support allied agencies in responding to, and recovering from, incidents ranging from minor traffic incidents through major disasters. |
| Traffic Operations Personnel | Center | 'Traffic Operations Personnel' represents the people that operate a traffic management center. These personnel interact with traffic control systems, traffic surveillance systems, incident management systems, work zone management systems, and travel demand management systems. They provide operator data and command inputs to direct system operations to varying degrees depending on the type of system and the deployment scenario. |
| Transportation Information Center | Center | The 'Transportation Information Center' collects, processes, stores, and disseminates transportation information to system operators and the traveling public. The physical object can play several different roles in an integrated ITS. In one role, the TIC provides a data collection, fusing, and repackaging function, collecting information from transportation system operators and redistributing this information to other system operators in the region and other TICs. In this information redistribution role, the TIC provides a bridge between the various transportation systems that produce the information and the other TICs and their subscribers that use the information. The second role of a TIC is focused on delivery of traveler information to subscribers and the public at large. Information provided includes basic advisories, traffic and road conditions, transit schedule information, yellow pages information, ride matching information, and parking information. The TIC is commonly implemented as a website or a web-based application service, but it represents any traveler information distribution service. |
| Vehicle Characteristics | Vehicle | 'Vehicle Characteristics' represents the external view of individual vehicles of any class from cars and light trucks up to large commercial vehicles and down to micromobility vehicles (MMVs). It includes vehicle physical characteristics such as height, width, length, weight, and other properties (e.g., magnetic properties, number of axles) of individual vehicles that can be sensed and measured or classified. This physical object represents the physical properties of vehicles that can be sensed by vehicle-based or infrastructure-based sensors to support vehicle automation and traffic sensor systems. The analog properties provided by this terminator represent the sensor inputs that are used to detect and assess vehicle(s) within the sensor's range to support safe AV operation and/or responsive and safe traffic management. |
Includes Functional Objects:
| Functional Object | Description | Physical Object |
|---|---|---|
| Roadway Basic Surveillance | 'Roadway Basic Surveillance' monitors traffic conditions using fixed equipment such as loop detectors and CCTV cameras. | ITS Roadway Equipment |
| Roadway Passive Monitoring | 'Roadway Passive Monitoring' monitors passing vehicles for a signature that can be used to recognize the same vehicle at different points in the network and measure travel times. Depending on the implementation and the penetration rate of the technology that is monitored, other point traffic measures may also be inferred by monitoring the number of vehicles within range over time. Today this approach is implemented most commonly using a Bluetooth receiver that passively monitors Bluetooth devices on-board passing vehicles and license plate readers that record the vehicle license plate number, but any widely deployed vehicle communications technology or feature that can be passively monitored to uniquely identify a vehicle could be used. | ITS Roadway Equipment |
| TMC Basic Surveillance | 'TMC Basic Surveillance' remotely monitors and controls traffic sensor systems and surveillance (e.g., CCTV) equipment, and collects, processes and stores the collected traffic data. Current traffic information and other real-time transportation information is also collected from other centers. The collected information is provided to traffic operations personnel and made available to other centers. | Traffic Management Center |
| TMC Passive Surveillance | 'TMC Passive Surveillance' collects time stamped vehicle identities from different detection zones, correlates the identities, and calculates link travel times and derives other traffic measures. | Traffic Management Center |
Includes Information Flows:
| Information Flow | Description |
|---|---|
| communications signature | Communications from vehicle or personal devices that can be monitored by ITS field equipment to uniquely identify the device. This flow represents communications from devices (via Bluetooth or Wi-Fi) that may be monitored by ITS field equipment or any other passive or active communications from the device that can be used to identify the device. This flow specifically covers passive monitoring of device communications. |
| passive vehicle monitoring control | Control commands used to control detection systems that rely on infrastructure-based identification of individual vehicles to measure travel times and other related measures by identifying the same vehicle at different points in the network. Related technologies include Bluetooth readers and license plate recognition systems. |
| passive vehicle monitoring coordination | The direct flow of information between field equipment. This includes control commands used to control detection systems that rely on infrastructure-based identification of individual vehicles to measure travel times and other related measures by identifying the same vehicle at different points in the network. Related technologies include Bluetooth readers and license plate recognition systems. The coordination also includes sharing of time stamped identifiers that identify the vehicles that have passed through a detection zone. |
| passive vehicle monitoring data | Time stamped identifiers that identify the vehicles that have passed through a detection zone. |
| road network conditions | Current and forecasted traffic information, road and weather conditions, and other road network status. Either raw data, processed data, or some combination of both may be provided by this flow. Information on diversions and alternate routes, closures, and special traffic restrictions (lane/shoulder use, weight restrictions, width restrictions, HOV requirements) in effect is included. |
| traffic detector control | Information used to configure and control traffic detector systems such as inductive loop detectors and machine vision sensors. |
| traffic detector coordination | The direct flow of information between field equipment. This includes information used to configure and control traffic detector systems such as inductive loop detectors and machine vision sensors Raw and/or processed traffic detector data is returned that allows derivation of traffic flow variables (e.g., speed, volume, and density measures) and associated information (e.g., congestion, potential incidents). This flow includes the traffic data and the operational status of the traffic detectors |
| traffic detector data | Raw and/or processed traffic detector data which allows derivation of traffic flow variables (e.g., speed, volume, and density measures) and associated information (e.g., congestion, potential incidents). This flow includes the traffic data and the operational status of the traffic detectors |
| traffic image meta data | Meta data that describes traffic images. Traffic images (video) are in another flow. |
| traffic images | High fidelity, real-time traffic images suitable for surveillance monitoring by the operator or for use in machine vision applications. This flow includes the images. Meta data that describes the images is contained in another flow. |
| traffic operator data | Presentation of traffic operations data to the operator including traffic conditions, current operating status of field equipment, maintenance activity status, incident status, video images, security alerts, emergency response plan updates and other information. This data keeps the operator appraised of current road network status, provides feedback to the operator as traffic control actions are implemented, provides transportation security inputs, and supports review of historical data and preparation for future traffic operations activities. |
| traffic operator input | User input from traffic operations personnel including requests for information, configuration changes, commands to adjust current traffic control strategies (e.g., adjust signal timing plans, change DMS messages), and other traffic operations data entry. |
| vehicle characteristics | The physical or visible characteristics of individual vehicles that can be used to detect, classify, and monitor vehicles and imaged to uniquely identify vehicles. |
| video surveillance control | Information used to configure and control video surveillance systems. |
| video surveillance coordination | The direct flow of information between field equipment. This includes information used to configure and control video surveillance systems and the high fidelity, real-time traffic images and associated meta data that are returned. |
Goals and Objectives
Associated Planning Factors and Goals
| Planning Factor | Goal |
|---|---|
| D. Increase the accessibility and mobility of people and for freight; | Reduce congestion |
| F. Enhance the integration and connectivity of the transportation system, across and between modes, for people and freight; | Enhance integration and connectivity |
| G. Promote efficient system management and operation; | Improve efficiency |
| J. Enhance travel and tourism. | Support travel and tourism |
Associated Objective Categories 
Associated Objectives and Performance Measures 

Needs and Requirements
| Need | Functional Object | Requirement | ||
|---|---|---|---|---|
| 01 | Traffic Operations need to be able to monitor the road network using infrastructure devices in order to detect and verify incidents and support implementation of traffic operational strategies. | Roadway Basic Surveillance | 01 | The field element shall collect, process, digitize, and send traffic sensor data (speed, volume, and occupancy) to the center for further analysis and storage, under center control. |
| Roadway Passive Monitoring | 01 | The field element shall collect, process, and send data to the center to uniquely identify passing vehicles in order to support travel time measurement | ||
| TMC Basic Surveillance | 01 | The center shall monitor, analyze, and store traffic sensor data (speed, volume, occupancy) collected from field elements under remote control of the center. | ||
| 02 | The center shall monitor, analyze, and distribute traffic images from CCTV systems under remote control of the center. | |||
| 06 | The center shall maintain a database of surveillance equipment and sensors and associated data (including the roadway on which they are located, the type of data collected, and the ownership of each). | |||
| 07 | The center shall remotely control devices to detect traffic. | |||
| TMC Passive Surveillance | 01 | The center shall collect time stamped vehicle identities from field equipment. | ||
| 02 | The center shall correlate the time stamped vehicle identities in order to calculate link travel times and derive other traffic measures. | |||
| 02 | Traffic Operations need to be able to monitor the infrastructure devices used for road network monitoring in order to detect faults in equipment or communications. | Roadway Basic Surveillance | 04 | The field element shall return sensor and CCTV system operational status to the controlling center. |
| 05 | The field element shall return sensor and CCTV system fault data to the controlling center for repair. | |||
| 03 | Traffic Operations need to be able to send network monitoring data to other centers in order to support traveler information. | TMC Basic Surveillance | 04 | The center shall distribute road network conditions data (raw or processed) based on collected and analyzed traffic sensor and surveillance data to other centers. |
Security
In order to participate in this service package, each physical object should meet or exceed the following security levels.
| Physical Object Security | ||||
|---|---|---|---|---|
| Physical Object | Confidentiality | Integrity | Availability | Security Class |
| Basic Vehicle | Not Applicable | Moderate | Low | Class 1 |
| ITS Roadway Equipment | Moderate | Moderate | Moderate | Class 2 |
| Other ITS Roadway Equipment | Moderate | Moderate | Moderate | Class 2 |
| Traffic Management Center | Moderate | Moderate | Moderate | Class 2 |
| Transportation Information Center | Low | Low | Moderate | Class 1 |
| Vehicle Characteristics | ||||
In order to participate in this service package, each information flow triple should meet or exceed the following security levels.
| Information Flow Security | |||||
|---|---|---|---|---|---|
| Source | Destination | Information Flow | Confidentiality | Integrity | Availability |
| Basis | Basis | Basis | |||
| Basic Vehicle | ITS Roadway Equipment | communications signature | Not Applicable | Moderate | Low |
| Byproduct flow, does contain PII (Bluetooth MAC addresses for example) but already existant and not required. | While the flow here is a byproduct of existing transmissions, if the data contained within is not reliable then the application using this data will generate erroneous results. Integrity is set MODERATE to emphasize to the application developer that they should verify the flows' integrity, or develop methods to minimize integrity's importance, in which case this could be LOW. | This is a by-product flow; taking advantage of existing wireless emissions to measure travel times for example. If this flow is not present then the application might not function, however, the application is not deploying this flow, it already exists. | |||
| ITS Roadway Equipment | Other ITS Roadway Equipment | passive vehicle monitoring coordination | Moderate | Moderate | Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| ITS Roadway Equipment | Other ITS Roadway Equipment | traffic detector coordination | Moderate | Moderate | Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| ITS Roadway Equipment | Other ITS Roadway Equipment | video surveillance coordination | Moderate | Moderate | Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| ITS Roadway Equipment | Traffic Management Center | passive vehicle monitoring data | Moderate | Moderate | Moderate |
| This is likely to include device identifiers or pseudonyms, which if intercepted could be used to track vehicles and PIDs. | This data will be used to determine travel times and other traffic metrics, which in turn will be used to manage traffic and offered to travelers as information for making their own travel decisions. | To be useful this flow needs to be updated reguarly. | |||
| ITS Roadway Equipment | Traffic Management Center | traffic detector data | Low | Moderate | Moderate |
| No impact if someone sees the data | Some minimal guarantee of data integrity is necessary for all C-ITS flows. THEA believes this to be LOW.only limited adverse effect if raw/processed traffic detector data is bad/compromised; DISC: WYO believes this to be HIGH | Only limited adverse effect of info is not timely/readily available, however without this information it will be difficult to perform traffic management activities, thus MODERATE. If not used for management, may be LOW. | |||
| ITS Roadway Equipment | Traffic Management Center | traffic image meta data | Low | Moderate | Moderate |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. | While accuracy of this data is important for decision making purposes, applications should be able to cfunction without it. Thus MODERATE generally. | While accuracy of this data is important for decision making purposes, applications should be able to function without it. Thus MODERATE generally. | |||
| ITS Roadway Equipment | Traffic Management Center | traffic images | Low | Moderate | Low |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. | Generally transportation coordination information should be correct between source and destination, or inappropriate actions may be taken. | While useful, there is no signficant impact if this flow is not available. | |||
| Other ITS Roadway Equipment | ITS Roadway Equipment | passive vehicle monitoring coordination | Moderate | Moderate | Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Other ITS Roadway Equipment | ITS Roadway Equipment | traffic detector coordination | Moderate | Moderate | Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Other ITS Roadway Equipment | ITS Roadway Equipment | video surveillance coordination | Moderate | Moderate | Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Traffic Management Center | ITS Roadway Equipment | passive vehicle monitoring control | Moderate | Moderate | Low |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. | Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Traffic Management Center | ITS Roadway Equipment | traffic detector control | Moderate | Moderate | Low |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. DISC: THEA, WYO believe this to be LOW: encrypted, authenticated, proprietary; but should not cause severe damage if seen | Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH.. From THEA: should be accurate and not be tampered with; could enable outside control of traffic sensors but should not cause severe harm, but could cause issues with traffic sensor data received and be detrimental to operations | Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH.. From THEA: want updates but delayed information will not be severe; should be able to operate from a previous/default control/config. DISC: WYO believes this to be MODERATE | |||
| Traffic Management Center | ITS Roadway Equipment | video surveillance control | Moderate | Moderate | Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. | Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Traffic Management Center | Traffic Operations Personnel | traffic operator data | Moderate | Moderate | Moderate |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. | Information presented to backoffice system operators must be consistent or the operator may perform actions that are not appropriate to the real situation. | The backoffice system operator should have access to system operation. If this interface is down then control is effectively lost, as without feedback from the system the operator has no way of knowing what is the correct action to take. | |||
| Traffic Management Center | Transportation Information Center | road network conditions | Low | Moderate | Moderate |
| No harm should come from seeing this data, as it is eventually intended for public consumption. | While accuracy of this data is important for decision making purposes, applications should be able to corroborate the data in many instances. Thus MODERATE generally. | Depends on the application; if mobility decisions that affect large numbers of travelers are made based on this data, then it is MODERATE. In more modest circumstances, it may be LOW. | |||
| Traffic Management Center | Transportation Information Center | traffic image meta data | Low | Moderate | Moderate |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. | While accuracy of this data is important for decision making purposes, applications should be able to cfunction without it. Thus MODERATE generally. | While accuracy of this data is important for decision making purposes, applications should be able to function without it. Thus MODERATE generally. | |||
| Traffic Management Center | Transportation Information Center | traffic images | Low | Moderate | Moderate |
| Intended for widespread and public distribution, so no reason to conceal. | While accuracy of this data is important for decision making purposes, applications should be able to cfunction without it. Thus MODERATE generally. | While availability of imagery is useful for decision making purposes, applications should be able to cfunction without it. Thus MODERATE generally, though it could be LOW. | |||
| Traffic Operations Personnel | Traffic Management Center | traffic operator input | Moderate | High | High |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | |||
Standards
The following table lists the standards associated with physical objects in this service package. For standards related to interfaces, see the specific information flow triple pages.
| Name | Title | Physical Object |
|---|---|---|
| ITE 5301 ATC ITS Cabinet | Intelligent Transportation System Standard Specification for Roadside Cabinets | ITS Roadway Equipment |
| NEMA TS 8 Cyber and Physical Security | Cyber and Physical Security for Intelligent Transportation Systems | ITS Roadway Equipment |
| Traffic Management Center |
System Requirements
| System Requirement | Need | ||
|---|---|---|---|
| 001 | The system shall monitor, analyze, and store traffic sensor data (speed, volume, occupancy) collected from field elements under remote control of the center. | 01 | Traffic Operations need to be able to monitor the road network using infrastructure devices in order to detect and verify incidents and support implementation of traffic operational strategies. |
| 002 | The system shall monitor, analyze, and distribute traffic images from CCTV systems under remote control of the center. | 01 | Traffic Operations need to be able to monitor the road network using infrastructure devices in order to detect and verify incidents and support implementation of traffic operational strategies. |
| 003 | The system shall distribute road network conditions data (raw or processed) based on collected and analyzed traffic sensor and surveillance data to other centers. | 03 | Traffic Operations need to be able to send network monitoring data to other centers in order to support traveler information. |
| 004 | The system shall maintain a database of surveillance equipment and sensors and associated data (including the roadway on which they are located, the type of data collected, and the ownership of each). | 01 | Traffic Operations need to be able to monitor the road network using infrastructure devices in order to detect and verify incidents and support implementation of traffic operational strategies. |
| 005 | The system shall remotely control devices to detect traffic. | 01 | Traffic Operations need to be able to monitor the road network using infrastructure devices in order to detect and verify incidents and support implementation of traffic operational strategies. |
| 006 | The system shall collect time stamped vehicle identities from field equipment. | 01 | Traffic Operations need to be able to monitor the road network using infrastructure devices in order to detect and verify incidents and support implementation of traffic operational strategies. |
| 007 | The system shall correlate the time stamped vehicle identities in order to calculate link travel times and derive other traffic measures. | 01 | Traffic Operations need to be able to monitor the road network using infrastructure devices in order to detect and verify incidents and support implementation of traffic operational strategies. |
| 008 | The system shall collect, process, digitize, and send traffic sensor data (speed, volume, and occupancy) to the center for further analysis and storage, under center control. | 01 | Traffic Operations need to be able to monitor the road network using infrastructure devices in order to detect and verify incidents and support implementation of traffic operational strategies. |
| 009 | The system shall return sensor and CCTV system operational status to the controlling center. | 02 | Traffic Operations need to be able to monitor the infrastructure devices used for road network monitoring in order to detect faults in equipment or communications. |
| 010 | The system shall return sensor and CCTV system operational status to the controlling center. | 02 | Traffic Operations need to be able to monitor the infrastructure devices used for road network monitoring in order to detect faults in equipment or communications. |
| 011 | The system shall return sensor and CCTV system fault data to the controlling center for repair. | 02 | Traffic Operations need to be able to monitor the infrastructure devices used for road network monitoring in order to detect faults in equipment or communications. |
| 012 | The system shall collect, process, and send data to the center to uniquely identify passing vehicles in order to support travel time measurement | 01 | Traffic Operations need to be able to monitor the road network using infrastructure devices in order to detect and verify incidents and support implementation of traffic operational strategies. |
Implementations


TM01.1 Detector-Based Surveillance Implementation
Infrastructure-based traffic detectors (e.g., inductive loops, machine vision, radar, acoustic detectors, etc.) are used to monitor traffic and collect traffic data that is used to support traffic operations and traveler information systems.
Detector-Based Surveillance Implementation Flows
| Information Flow | Description | Inclusion Status |
|---|---|---|
| road network conditions | Current and forecasted traffic information, road and weather conditions, and other road network status. Either raw data, processed data, or some combination of both may be provided by this flow. Information on diversions and alternate routes, closures, and special traffic restrictions (lane/shoulder use, weight restrictions, width restrictions, HOV requirements) in effect is included. | Optional |
| traffic detector control | Information used to configure and control traffic detector systems such as inductive loop detectors and machine vision sensors. | Fundamental |
| traffic detector coordination | The direct flow of information between field equipment. This includes information used to configure and control traffic detector systems such as inductive loop detectors and machine vision sensors Raw and/or processed traffic detector data is returned that allows derivation of traffic flow variables (e.g., speed, volume, and density measures) and associated information (e.g., congestion, potential incidents). This flow includes the traffic data and the operational status of the traffic detectors | Optional |
| traffic detector data | Raw and/or processed traffic detector data which allows derivation of traffic flow variables (e.g., speed, volume, and density measures) and associated information (e.g., congestion, potential incidents). This flow includes the traffic data and the operational status of the traffic detectors | Fundamental |
| traffic operator data | Presentation of traffic operations data to the operator including traffic conditions, current operating status of field equipment, maintenance activity status, incident status, video images, security alerts, emergency response plan updates and other information. This data keeps the operator appraised of current road network status, provides feedback to the operator as traffic control actions are implemented, provides transportation security inputs, and supports review of historical data and preparation for future traffic operations activities. | Optional |
| traffic operator input | User input from traffic operations personnel including requests for information, configuration changes, commands to adjust current traffic control strategies (e.g., adjust signal timing plans, change DMS messages), and other traffic operations data entry. | Optional |
| vehicle characteristics | The physical or visible characteristics of individual vehicles that can be used to detect, classify, and monitor vehicles and imaged to uniquely identify vehicles. | Optional |
Detector-Based Surveillance Implementation Functional Objects
| Functional Object |
|---|
| Roadway Basic Surveillance |
| TMC Basic Surveillance |
Back to Implementation List
TM01.2 Video Monitoring Implementation
Cameras in the field are used to collect and share traffic images that are used by operating agencies to manage traffic and shared with the traveling public to convey traffic flow and congestion information.
Video Monitoring Implementation Flows
| Information Flow | Description | Inclusion Status |
|---|---|---|
| traffic image meta data | Meta data that describes traffic images. Traffic images (video) are in another flow. | Optional |
| traffic image meta data | Meta data that describes traffic images. Traffic images (video) are in another flow. | Fundamental |
| traffic images | High fidelity, real-time traffic images suitable for surveillance monitoring by the operator or for use in machine vision applications. This flow includes the images. Meta data that describes the images is contained in another flow. | Optional |
| traffic images | High fidelity, real-time traffic images suitable for surveillance monitoring by the operator or for use in machine vision applications. This flow includes the images. Meta data that describes the images is contained in another flow. | Fundamental |
| traffic operator data | Presentation of traffic operations data to the operator including traffic conditions, current operating status of field equipment, maintenance activity status, incident status, video images, security alerts, emergency response plan updates and other information. This data keeps the operator appraised of current road network status, provides feedback to the operator as traffic control actions are implemented, provides transportation security inputs, and supports review of historical data and preparation for future traffic operations activities. | Optional |
| traffic operator input | User input from traffic operations personnel including requests for information, configuration changes, commands to adjust current traffic control strategies (e.g., adjust signal timing plans, change DMS messages), and other traffic operations data entry. | Optional |
| vehicle characteristics | The physical or visible characteristics of individual vehicles that can be used to detect, classify, and monitor vehicles and imaged to uniquely identify vehicles. | Optional |
| video surveillance control | Information used to configure and control video surveillance systems. | Fundamental |
| video surveillance coordination | The direct flow of information between field equipment. This includes information used to configure and control video surveillance systems and the high fidelity, real-time traffic images and associated meta data that are returned. | Optional |
Video Monitoring Implementation Functional Objects
| Functional Object |
|---|
| Roadway Basic Surveillance |
| TMC Basic Surveillance |
Back to Implementation List
TM01.3 Bluetooth Signature Monitoring Implementation
The infrastructure includes Bluetooth readers that can identify passing vehicles by their Bluetooth signature and use that information to calculate travel times and other traffic measures.
Bluetooth Signature Monitoring Implementation Flows
| Information Flow | Description | Inclusion Status |
|---|---|---|
| communications signature | Communications from vehicle or personal devices that can be monitored by ITS field equipment to uniquely identify the device. This flow represents communications from devices (via Bluetooth or Wi-Fi) that may be monitored by ITS field equipment or any other passive or active communications from the device that can be used to identify the device. This flow specifically covers passive monitoring of device communications. | Fundamental |
| passive vehicle monitoring control | Control commands used to control detection systems that rely on infrastructure-based identification of individual vehicles to measure travel times and other related measures by identifying the same vehicle at different points in the network. Related technologies include Bluetooth readers and license plate recognition systems. | Fundamental |
| passive vehicle monitoring coordination | The direct flow of information between field equipment. This includes control commands used to control detection systems that rely on infrastructure-based identification of individual vehicles to measure travel times and other related measures by identifying the same vehicle at different points in the network. Related technologies include Bluetooth readers and license plate recognition systems. The coordination also includes sharing of time stamped identifiers that identify the vehicles that have passed through a detection zone. | Optional |
| passive vehicle monitoring data | Time stamped identifiers that identify the vehicles that have passed through a detection zone. | Fundamental |
| road network conditions | Current and forecasted traffic information, road and weather conditions, and other road network status. Either raw data, processed data, or some combination of both may be provided by this flow. Information on diversions and alternate routes, closures, and special traffic restrictions (lane/shoulder use, weight restrictions, width restrictions, HOV requirements) in effect is included. | Optional |
| traffic operator data | Presentation of traffic operations data to the operator including traffic conditions, current operating status of field equipment, maintenance activity status, incident status, video images, security alerts, emergency response plan updates and other information. This data keeps the operator appraised of current road network status, provides feedback to the operator as traffic control actions are implemented, provides transportation security inputs, and supports review of historical data and preparation for future traffic operations activities. | Optional |
| traffic operator input | User input from traffic operations personnel including requests for information, configuration changes, commands to adjust current traffic control strategies (e.g., adjust signal timing plans, change DMS messages), and other traffic operations data entry. | Optional |
Bluetooth Signature Monitoring Implementation Functional Objects
| Functional Object |
|---|
| Roadway Passive Monitoring |
| TMC Basic Surveillance |
| TMC Passive Surveillance |
Back to Implementation List
